In recent years, the security problems of Web applications faced by various organizations of governments and enterprises have become more and more complex, and security threats are growing rapidly, especially the mixed threat risks, such as hacker attacks, worms, DDoS attacks, SQL injection, cross site scripting, and the use of Web application security vulnerabilities, which have greatly troubled users and caused serious damage to information networks and core businesses, Internal maintenance personnel are tired of dealing with the remedy of web application security vulnerabilities firewall Limited to its own detection mechanism and protection depth, it has been difficult to solve many current Web application security problems.
Web Application Firewall (WAF for short) is a new product in the international security community, which is used to solve the security problems in the Web application layer
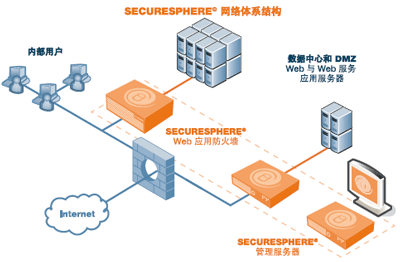
Imperva SecureSphere? Web application firewall
The only automated web application firewall in the industry
Is your web application secure?
Web application is the main target of attack; According to the FBI survey in 2006, 92% of enterprises have been attacked by successful web applications in the past 12 months. These attacks can lead to devastating results ranging from serious damage to profile data to brand damage, legal proceedings and fines.
Both the security administrator and the management organization have noticed this fact. Since traditional security products cannot prevent web application attacks, new compliance regulations now mandate application layer protection. For many enterprises, meeting current security and compliance requirements is a thorny problem.
Protect your applications and business with Imperva
Imperva's SecureSphere Web application firewall can protect Web applications and sensitive data. Moreover, the firewall has the characteristics of simple deployment, automation, adjustable security, low operating costs, etc. SecureSphere provides your enterprise with a set of practical and highly secure solutions to ensure that the enterprise can solve the latest challenges related to transaction data security and compliance.

Automated web application security
SecureSphere ® The Web application firewall implements automatic Web attack protection, thus changing the way enterprises protect applications and sensitive data. Imperva's dynamic modeling technology automatically builds a legal behavior model and automatically adjusts it according to application changes in the future, so as to keep the application protection of SecureSphere always up to date and accurate, without manual configuration or adjustment. The deployment of SecureSphere can be completed within a few minutes. It does not need to modify the original infrastructure, and it can protect individual applications from The server And the whole application system of the network. Imperva's transparent inspection technology has a throughput capacity of thousands of megabits and a waiting time as short as sub millisecond. It also provides a variety of high availability options to meet the most demanding data center requirements. For large-scale deployment, the SecureSphere MX management server can centralize and simplify configuration, monitoring and reporting.
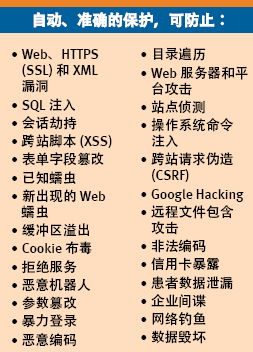
Comprehensive attack protection
SecureSphere Web application firewall uses multiple security protection to provide the highest level of protection. These protections include dynamic configuration files, HTTP protocol verification, platform attack security, and associated attack confirmation.
Automatic Applied Learning – Imperva's Dynamic Modeling
SecureSphere's unique dynamic modeling technology can automatically learn the structure, elements and expected usage patterns of protected Web applications. The dynamic model continuously and automatically detects effective application modifications and incorporates them into the application rule file. By comparing Web requests with model rules, SecureSphere can detect unacceptable behaviors with high precision and prevent malicious activities.
The dynamic configuration file overcomes the biggest defect related to the absolute security model: it needs to manually create and update a huge white list that may contain hundreds or even thousands of URLs, form fields, parameters, and cookies. Dynamic configuration file technology can automatically build accurate configuration files without manual configuration or adjustment.
Latest security solutions from Imperva ADC
Imperva Application Protection Center (ADC) is an internationally renowned security research institution. They continue to investigate new vulnerabilities reported around the world, analyze abuse traffic from various real Web sites, and conduct preliminary vulnerability studies to identify the latest threats. The result of this research is the latest protection measures on each layer of SecureSphere, including signature update, protocol verification rules and association rules.
In addition to the latest attack protection, ADC also provides optional ADC knowledge services. ADC knowledge provides in-depth business application knowledge, pre built compliance reports, and best practices from compliance and security experts.
HTTP protocol verification
HTTP protocol verification can prevent massive protocol abuse, including buffer overflow, malicious coding, HTTP * * * * and illegal server operations. Flexible rules allow users to strictly comply with RFC standards or allow minor deviations from specific applications.
Platform and network attack protection
SecureSphere prevents attacks targeting known web server vulnerabilities, middleware vulnerabilities, and platform vulnerabilities. From Bugtraq, CVE Snort.、 More than 4000 signatures from Imperva ADC and other sources provide comprehensive protection against such attacks. In addition to identifying known worms, SecureSphere also identifies emerging new Web worms by detecting unique attribute combinations with Web worm attack characteristics.
SecureSphere integrates the stateful network firewall, which can resist illegal users, protocols and network attacks from internal and external sources. It meets mandatory best practice security requirements and can prevent sensitive web applications from being used by unnecessary protocols.
Web Service Protection
Using its dynamic configuration file technology, SecureSphere can also create legal Web service behavior models including XML files, elements, attributes, schemas, variables, and SOAP operations. Any attempt to tamper with normal Web service behavior will be detected and blocked.
Unmatched accuracy
Imperva's unique correlation attack confirmation technology associates the cross security layer and long-term violations to accurately identify the most complex attacks. Individual violations may not be able to identify attacks accurately, but they can be identified without question by associating unique combinations of violations. No other solution can match the accuracy achieved through correlation attack verification.
Transparent deployment
No application or network modification required
The transparent inspection technology uniquely enables SecureSphere to be deployed in any environment without modifying the original applications, servers or networks. SecureSphere provides comprehensive and accurate application security, and does not require enterprises to redesign web applications, modify IP or DNS settings, or update authentication schemes.
The kernel based transparent check separates the security from the deployment mode, so that SecureSphere can support the following operation modes:
. Transparent bridge – simple to deploy, able to provide the best performance in the industry
. Router – Used for network segmentation, routing and network address translation
. Reverse proxy - used for content modification, such as cookie signature and URL rewriting
. Transparent proxy - used to quickly deploy content modification without changing the network
. Off line monitoring program – zero risk monitoring and analysis.
Gigabit performance
SecureSphere provides a throughput of thousands of megabits per second, tens of thousands of transactions, and can maintain the waiting time at the sub millisecond level. This performance level is one order of magnitude higher than the competitor's method, which ensures a completely transparent deployment. After using SecureSphere, security will never affect data center service level agreements or application performance.
High availability
SecureSphere supports many high availability options, which enables it to be deployed in some of the world's largest networks. Availability options include:
Imperva high availability (IMPPHA) provides sub second failover
Virtual Router Redundancy Protocol (VRRP) for router or agent deployment
Active active and active passive redundancy for external availability mechanisms
The interface for fault short circuit is used to ensure the availability of a single gateway
. Non online deployment for zero risk monitoring and evaluation
operation
Automated rule maintenance
The implementation of the traditional white list security model requires continuous manual adjustment. When the Web application is modified, the whitelist of the application firewall must be updated. The automatic modeling technology can automatically establish the model of the Web application and automatically adjust the model according to the application modification, so manual adjustment is no longer required. SecureSphere administrators can still modify the application rule model and create customized rules.
Centralized management
SecureSphere can be deployed as an independent device or extended to protect distributed data centers. For large environments, including hybrid Web and database deployments, the SecureSphere MX management server can provide centralized configuration, monitoring, and reporting. The management server simplifies the management of large enterprise environment and ASP environment through hierarchical organization grouping, granular management permissions and unique task oriented workflow.
Enterprise level report
SecureSphere provides rich graphical report functions, enabling customers to easily understand security status and meet regulatory compliance requirements. SecureSphere provides both predefined and fully customizable web-based reports. You can view reports on demand, or send reports by email daily, weekly, or monthly. SecureSphere's reporting platform provides an immediate and comprehensive way to understand security, compliance, and content delivery issues.
Monitoring and alarm
The real-time dashboard provides a high-level system status and security event view. Alarms can be easily searched and sorted, and can also be directly linked to the corresponding security rules. To flexibly integrate with security event management products, SecureSphere supports syslog, SNMP, and direct ODBC access.
Apply User Tracking
SecureSphere's dynamic modeling technology automatically obtains the name of the Web application user and associates all subsequent session activities with this specific user name. As a result, SecureSphere can uniquely monitor, enforce, and audit rules by user.
Optional database protection
The SecureSphere Web application firewall has been extended to monitor and protect Oracle, MS-SQL Server, DB2, Sybase and Informix databases. SecureSphere database security gateway can prevent external attacks and internal personnel abuse, thus providing end-to-end security for the data center. In addition, it can also use SecureSphere's application user tracking to trace individual SQL queries to Web users. This common user tracking capability provides unparalleled knowledge of database requests, modifications, and violations.
Typical customers




![]()












